Healthcare Provider Directory Boosts Direct Secure Messaging Value
The Direct Secure Messaging network overseen by DirectTrust.org is growing rapidly. At mid-year 2019, there are over 190,000 clinical organizations using Direct, and almost 2 million addresses have been issued. This critical mass has the power to enable interoperable health information exchange between disparate systems nationwide, but recipient addresses must be easily discoverable in order to achieve this. Luckily, many health information service providers (HISPs) provide access to a DirectTrust federated directory known as the Healthcare Provider Directory (HPD). This directory grants you access to a constantly growing Direct subscriber database, allowing you to easily discover recipient addresses.
What to Look For in a Healthcare Provider Directory (HPD):
When choosing an HPD, there are a variety of different features that you should be on the lookout for. Some of the key features that we recommend you search for are:
- The ability to search for a recipient by multiple criteria, including:
- Provider name
- National Provider Identifier (NPI)
- Medical specialty
- Function/role
- Etc.
- HPD sharing agreements with other Health Information Service Providers (HISPs) and the DirectTrust organization
- Integration with the nationwide NPI registry. This enables updates and appends data for individual records in the directory
So, How Can the DataMotion HPD Meet Your Needs?
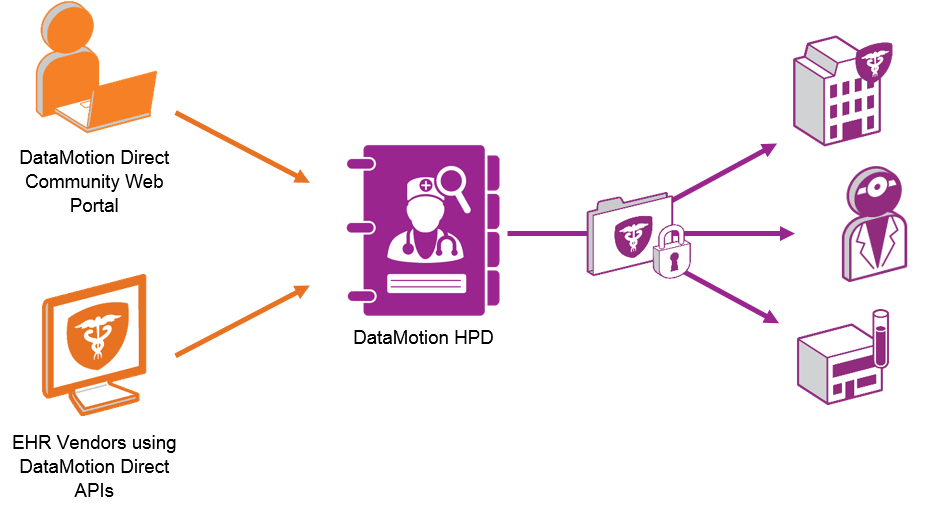
DataMotion Direct Community Web Portal Users
All users of our DataMotion Direct Community Web Portal (CWP) have access to the DataMotion HPD through the search field integrated into the CWP Address Book function. This address book allows you to search by a variety of criteria including by provider name, organization, location, NPI, or specialty, making it easy to find your intended recipient address. Once an address is found, all you have to do is set the address in a message or save it to your address book.
DataMotion Direct Integration Partners
Are you a DataMotion Direct Integration Partner? If you are, then you receive comprehensive access to the DataMotion HPD via the HPD Web Services API for EHR software vendors and other health IT solution providers. This allows HPD integration into an application user interface. The web services API exposes search functionality using the same parameters so it can be integrated into existing software and workflows.
What Kinds of Features and Benefits are We Able to Offer Your Organization?
- Extensive Data Set – With over 20 searchable data fields, you can expect much better search accuracy
- NPI Registry Integration – Our HPD regularly checks the NPI Registry, meaning it is constantly up-to-date and appending data for individual records in the directory
- API access – Allows you to integrate HPD search/retrieval into your existing applications and workflows
- HISP partnerships – Allows us to continuously expand the DataMotion HPD and make DataMotion Direct addresses discoverable to other providers across the country