Elevate Productivity, Compliance and CX with Secure Message APIs & No-Code Integrations
Enhance Salesforce, Genesys, Okta, Microsoft 365, Teams and customer apps with secure document and message exchange.
JenAI Assist™
AI-Powered. Human-Backed.
A smart, secure, and compliant digital engagement solution that brings controlled GenAI chat to you and your clients.
JenAI Assist™
AI-Powered. Human-Backed.
A smart, secure, and compliant digital engagement solution that brings controlled GenAI chat to you and your clients.
TRUSTED BY THOUSANDS OF FORWARD-THINKING COMPANIES AND MILLIONS OF USERS!
How We Can Help
Enjoy a communication experience that’s easier than ever with DataMotion’s secure exchange.
2023 Top Rated
We’re excited to have been recognized by TrustRadius as a 2023 Top Rated Award recipient across four categories:
○ Email Encryption
○ Direct Secure Messaging
○ Manage File Transfer
○ Data Loss Prevention
Securely Exchange in Your Self-Service Portal
By incorporating DataMotion into your self-service portal, you can improve your customers’ digital experience by leaps and bounds. They can easily ask questions and share documents in one place. Through better online support, you can find many improvements that add to your bottom line, improve communication and reduce development time.
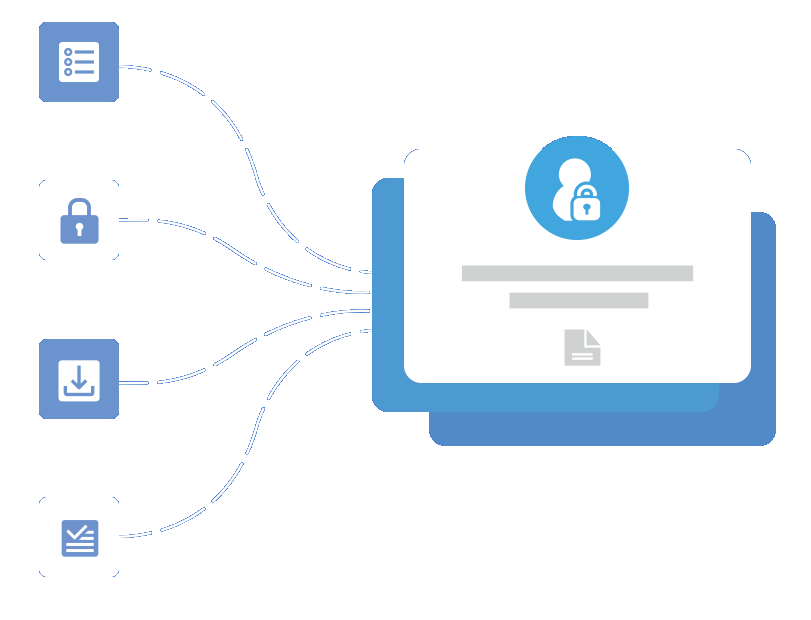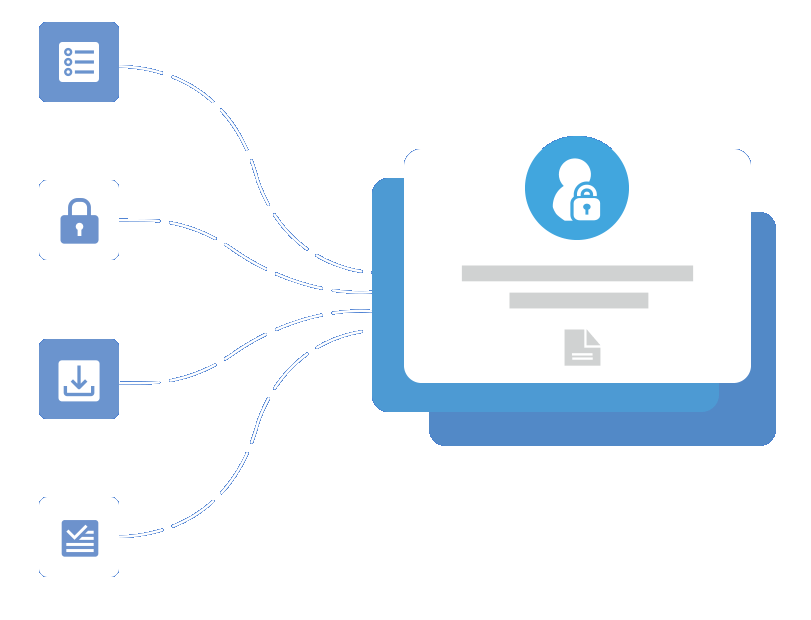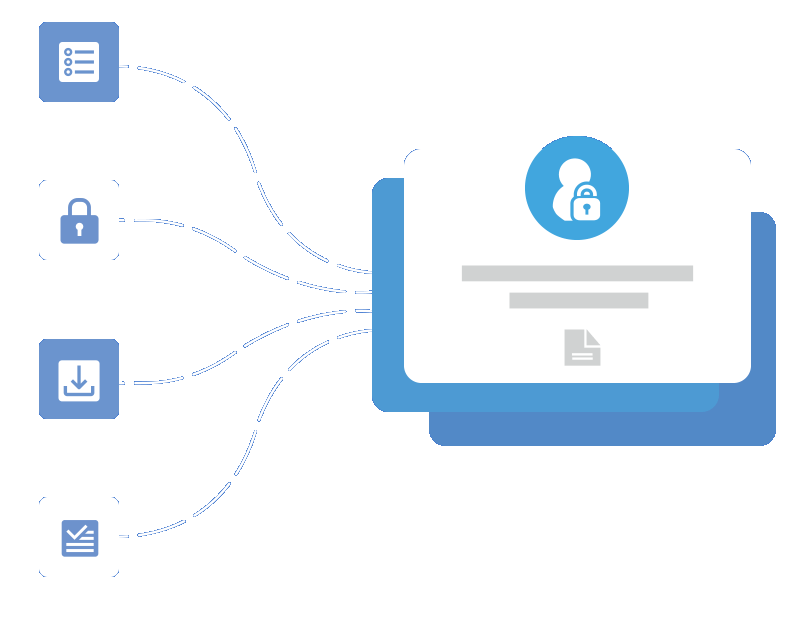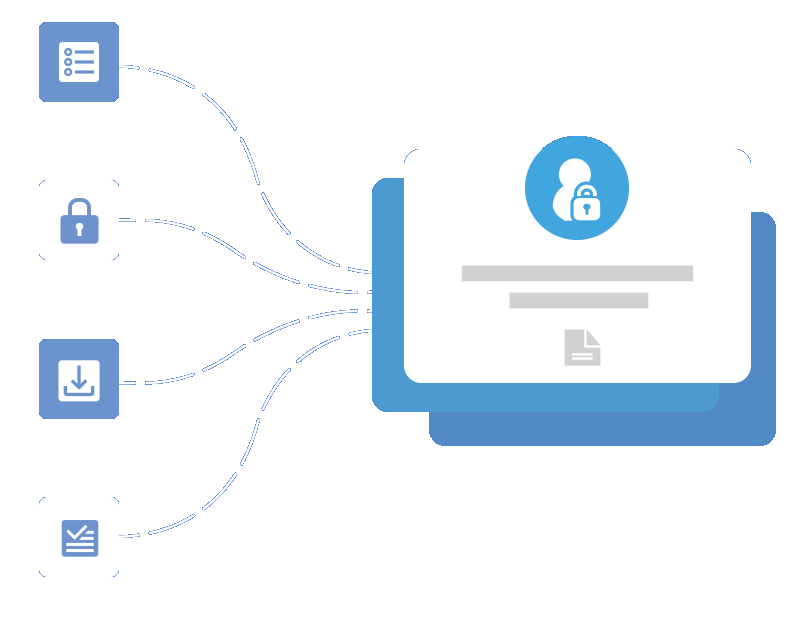
Get Your CRM to Exchange Securely
Delays and errors in back-office processes are the second-largest cause of customer dissatisfaction. These issues lead to greater problems for the entire business, such as poor efficiency and bad customer service. With a better approach to these processes, you can experience smooth, simple collaboration with internal back-end systems.
Use Pre-Built Options for More Efficient Work
Don’t want to mess with integration? No problem! We have several pre-built options, perfect for organizations with limited resources. These options help you easily balance customers and meet needs while increasing efficiency.
Build Your Own Secure Exchange
DataMotion APIs seamlessly blend secure messaging and document exchange with your new or existing workflows and applications.
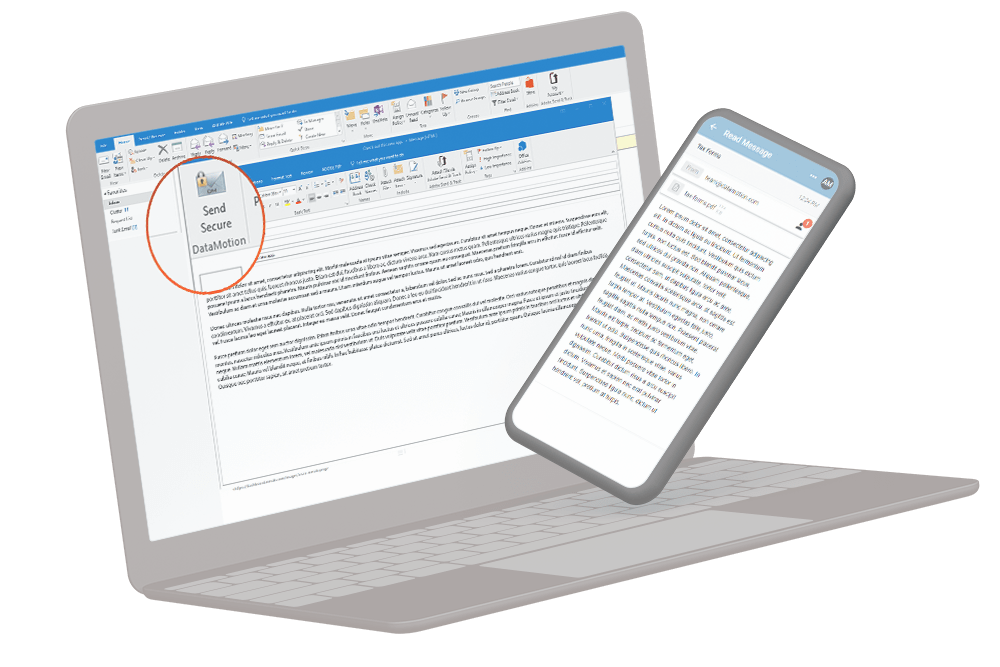
Integrate Secure Exchange into Your Mobile App
Build trust and improve security by making your app safer to use with the DataMotion secure message API. You can cut down on development time, meet regulatory requirements for exchanging sensitive data and increase customer confidence and loyalty with a seamless, built-in tool.
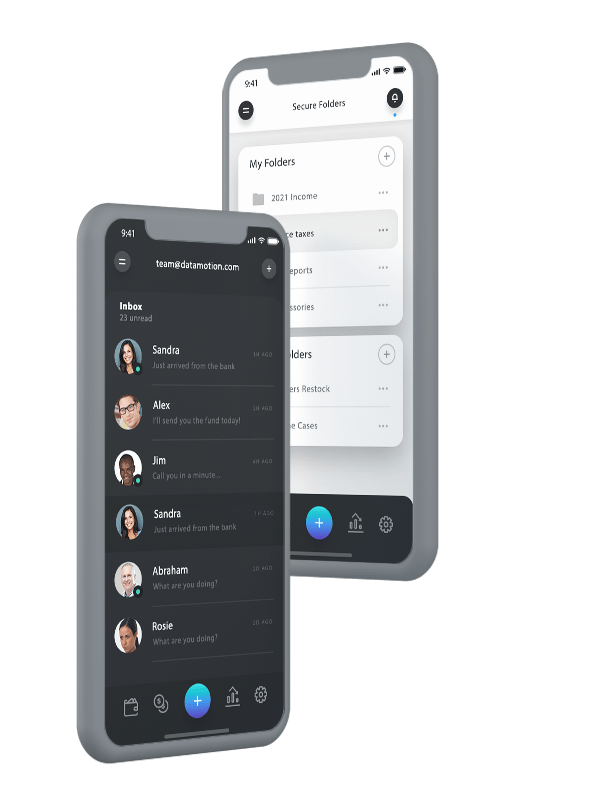
Add Seamless, Secure Exchange to Workflows and Apps
Want to make your data communications feel like a native part of your existing workflow or application? The secure document exchange and messaging API can help. It provides you with seamless operation, perfect for unique and custom-use cases. It can also save on development time and help you create a more secure and customer-friendly workflow.
The DataMotion Building Blocks
If you want to create a secure messaging system on your own, you must consider how you’ll create the significant ecosystem required. You could spend hours building this yourself, but you don’t have to. We’ve already done the hard work for you.