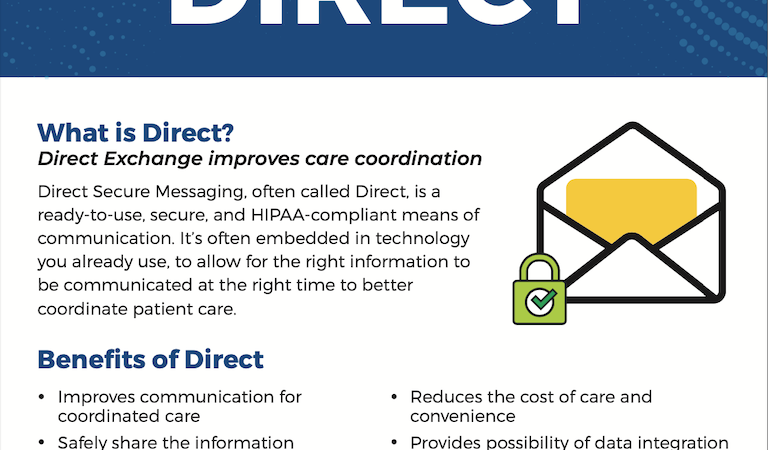
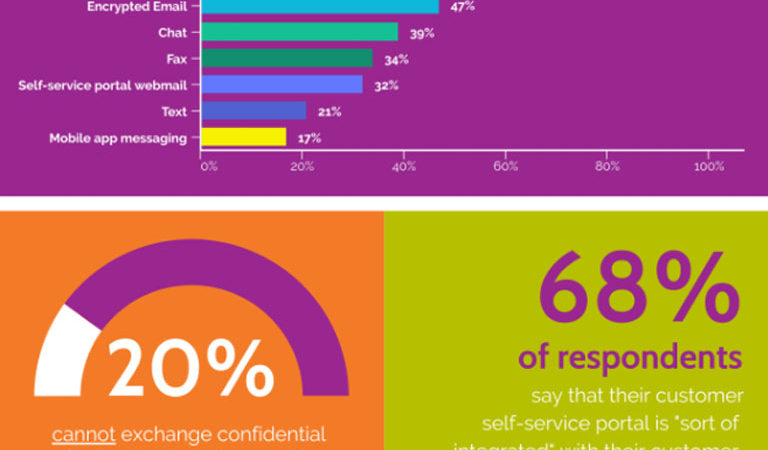
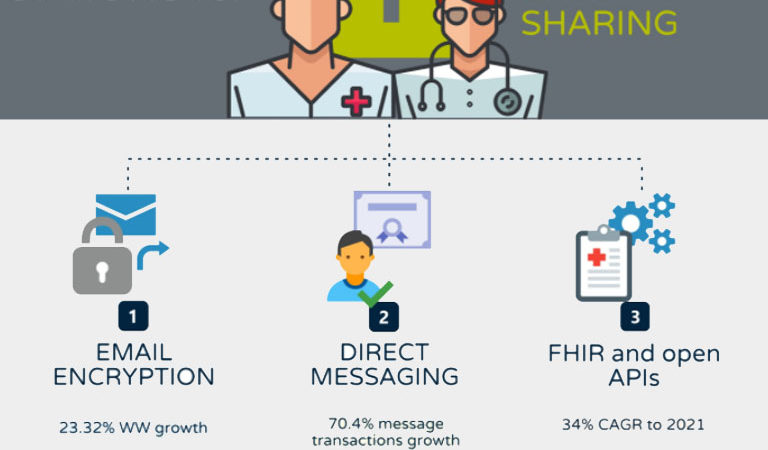
DataMotion Blog
Dive deep into the latest industry trends, case studies, and statistics. Our blog offers insights and expert
perspectives to keep you informed and prepared in a rapidly evolving digital landscape.
FINANCIAL SERVICES
Enabling Next-Level Efficiency in Financial Services with DataMotion’s Lightning Application
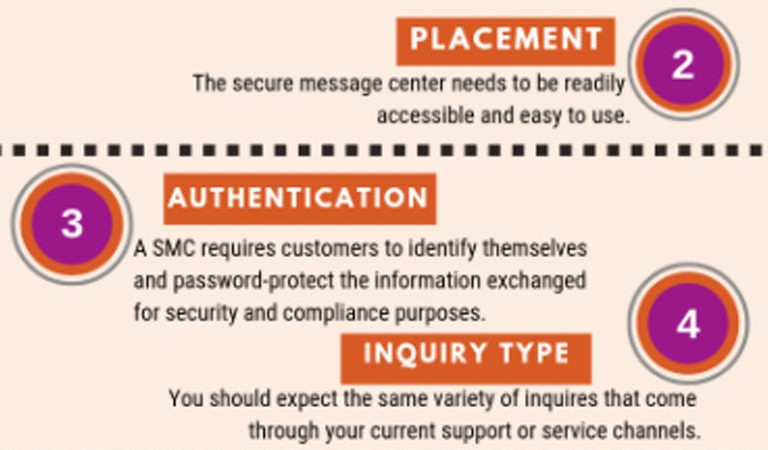
Pair Salesforce Lightning with the DataMotion secure message center to create a dynamic solution that enhances communication and ensures the robust protection of sensitive data. Read more.